A sophisticated supply chain attack has targeted Kaseya VSA, a solution used for remote endpoint and network monitoring, impacting more than 1000 businesses with the deployment of ransomware.
At this point, the on-premise deployments on servers have been reported to be vulnerable. Given the visibility and level of access that VSA has inside an organization, the attackers can compromise entire enterprise networks. Kaseya have shut down their software-as-a-service (SaaS) servers as a precautionary measure and it is advised to shutdown any on-premise VSA server.
Ransomware infection
Many Kaseya servers are being used to deploy the Revil (AKA Sodinokibi) ransomware, since VSA is designed to allow administration of systems with high level privileges. The ransomware will be deployed form a task disguised as “Kaseya VSA Agent Hot-fix” that will leverage PowerShell and will disable multiple features from Windows Defender to evade detection and sandbox submission.
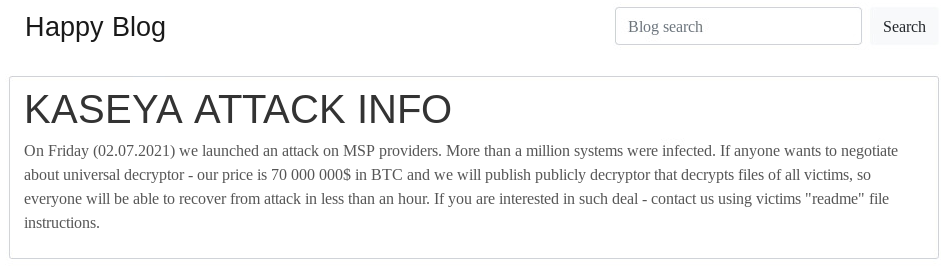
The REvil gang have not posted details on their victims on their blog yet, but request a ransom of 70 million USD in bitcoin for the decryptor as shown in the picture below
Mitigation actions
- Currently Disable the on-premise Kaseya VSA servers as soon as possible
- Once the patch is available by Kaseya, ensure that the mitigation steps to increase your security posture are installed prior to restarting the VSA. Updates on the situation by Kaseya can be found here.
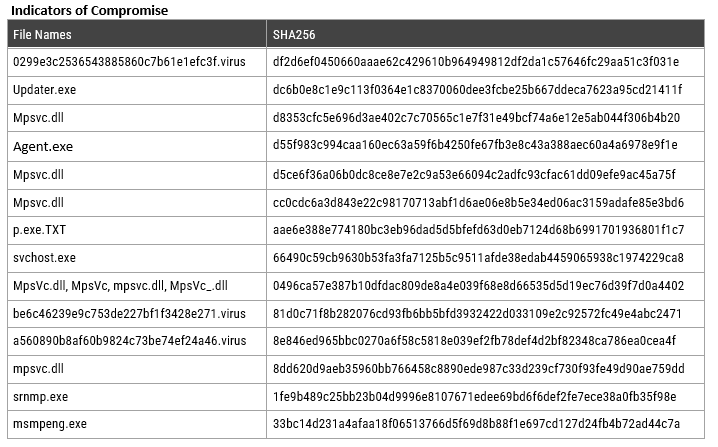
- If you suspect your on-premise VSA may be compromised, collect and examine that the logs in the following locations:
• C:\ProgramData\Kaseya\Log\KaseyaEdgeServices\*.log
• C:\inetpub\logs\LogFiles\W3SVC#\*.log
• C:\ProgramData\Kaseya\Kupload\KUpload.log - To assist organizations in the investigation, Kaseya provides a detection tool, along with runtime instructions to analyze VSA servers or managed endpoint in the link
- Ensure that other remote administrative utilities like PowerShell, WMI are being used only when needed and a proper user access control with privileges is being used.



