On February 8, 2022, three vulnerabilities (CVE-2022-22536, CVE-2022-22532, and CVE-2022-22533) the first of these with CVSS 10.0 in SAP Internet Communication Manager (ICM) and SAP Web Dispatcher were fixed as part of SAP Security Patch Day of February 2022. Affected customers should apply the SAP security patches immediately or use the available workaround.
This discovery will require immediate attention by most SAP customers given the widespread usage of the vulnerable technology component in SAP landscapes around the world.
The exploitation of CVE-2022-22536 uses an un-auth HTTP request smuggling bug that can be used to steal SAP session data and credentials.
It resides in the SAP ICM, which is the HTTPS server component included in almost all SAP products that need internet connectivity.
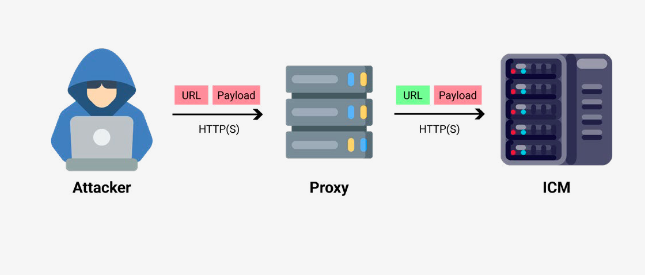
SAP Product Security Response Team has worked to address these issues and will provide technical details and proof of concepts.
Remediation
SAP has released security updates to address the CVE-2022-22536, CVE-2022-22532, and CVE-2022-22533. Admins are advised to prioritize applying the Security Notes 3123396 and 3123427 (https://wiki.scn.sap.com/wiki/display/PSR/SAP+Security+Patch+Day+-+February+2022) to their affected SAP applications immediately. If exploited, these vulnerabilities, dubbed ICMAD (Internet Communication Manager Advanced Desync), enable attackers to execute serious malicious activities on SAP users, business information, and processes — and ultimately compromise unpatched SAP applications



