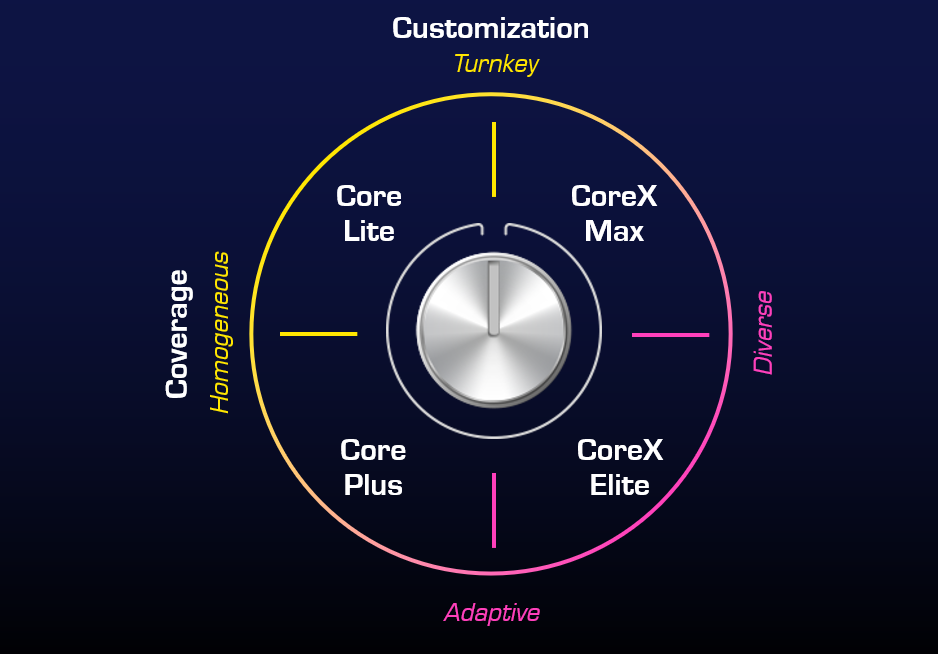
Modular MDR Products
OBRELA MDR is scalable and designed for organizations of all sizes, integrating AI-driven cybersecurity, predictive analytics, and automated threat modeling. Obrela’s services cover endpoints, identities, apps, email, SaaS, networks, and cloud environments, with advanced detection powered by EDR, XDR, and SIEM technologies.
Choose Your Level of Coverage
A solid foundation for threat detection and response, centered around Microsoft Defender XDR. Ideal for establishing baseline protection across cloud and on-premises environments, enhanced with OBRELA’s advanced analytics and automation.
- Designed to place EDR and XDR at the center of your SOC operations.
- Establishes a strong foundation for threat management across cloud and on-premises environments.
- Enhanced with OBRELA’s SIEM-based analytics, AI-driven anomaly detection, and automated application security analytics.

The most advanced, all-in-one, extended (X) MDR solution. Combines full Microsoft XDR and Sentinel capabilities with OBRELA’s proprietary threat content for unmatched visibility, speed, and accuracy—ensuring no blind spots across your digital estate.
- Delivers the most advanced, extended (X), an all-in-one service.
- Combines EDR, XDR, and SIEM for maximum visibility and coverage.
- Features predictive threat modeling and real-time AI-powered controls.
- Constantly updated with elite threat telemetry and detection content.
- Seamlessly integrates with any asset or data source—ensuring no blind spots.


Why OBRELA MDR?
By integrating the latest in AI, SecDevOps, and predictive analytics, OBRELA MDR empowers you to stay ahead of ever-evolving threats. Our combination of automated defense, human insight, and continuous innovation ensures next-generation cybersecurity that protects what matters most.


NEXT GENERATION MDR | BROCHURE
OBRELA MDR is scalable and designed for organizations of all sizes, integrating AI-driven cybersecurity, predictive analytics, and automated threat modeling.

Gartner recognised
OBRELA’s multiple Gartner recognitions confirm its leadership in the Managed Detection and Response (MDR) market, showcasing its strategic vision, technical innovation, and ability to deliver real-world cybersecurity outcomes. This recognition assures clients of OBRELA’s commitment to the highest industry standards.

MISA Accredited
Membership in the Microsoft Intelligent Security Association (MISA) further strengthens OBRELA’s credibility. As part of this exclusive alliance, OBRELA integrates seamlessly with Microsoft technologies like Sentinel and Defender, offering enhanced protection for Microsoft-powered environments. Together, these endorsements demonstrate OBRELA MDR’s innovation, reliability, and industry backing.


ACCESS THE GARTNER MDR GUIDE
Obrela has been included in Gartner's MDR Market Guide. Download to learn more about the latest MDR Service providers