Overview
2 new zero-day vulnerabilities in Microsoft Exchange Server, which are being exploited in the wild, have been reported. These identified vulnerabilities by Microsoft were reported (not currently published) and registered/reserved as CVE-2022-41040 and CVE-2022-41082. These security flaws allow for remote code execution (RCE) when PowerShell is accessible to the attacker. The respective vulnerabilities were previously discovered, confirmed, and accepted by ZDI (zero-day initiative) as ZDI-CAN-18333 and ZDI-CAN-18802.
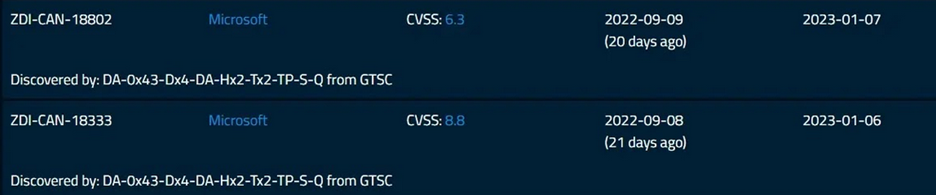
ZDI-CAN-18333, CVSS: 8.8 – ZDI-CAN-18802, CVSS: 6.3
https://cve.mitre.org/cgi-bin/cvename.cgi?name=2022-41040
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-41082
Brief Description
After the respective vulnerabilities are exploited, malicious actors have the ability for remote code execution which in this case initiate web shells on the affected Exchange Servers hosts. The Actors may then inject malicious DLLs into the memory, suspicious files on the attacked servers, and execute these files through the Windows Management Instrumentation Command line (WMIC). That effort leads to the ability to conduct remote code execution on other assets of the infrastructure, as well. Furthermore, it has been observed that web shells with Chinese characteristics were bing dropped into Exchange servers.
Currently, Microsoft is aware only of limited targeted attacks that are using the two vulnerabilities to get into users’ systems. In these attacks, CVE-2022-41040 enables an authenticated attacker to remotely trigger CVE-2022-41082. It should be noted that authenticated access to the vulnerable Exchange Server is necessary to successfully exploit either of these two vulnerabilities.
Potentially Affected Assets
Microsoft Exchange Servers at the first stage and ANY other asset become reachable to the malicious actor exploiting the respective flaws during the lateral movement stage.
Potential Impact
Not measurable at the moment: Even though the exploitation of the flaws gives the malicious actor the ability to conduct RCE (Remote Code Execution) and lateral movement on the network (already reported in the wild) the impact of such an action can be severe but difficult to be measured for the time being.
Potential Actors
Chinese Attack Groups (web shell codepage is 936 – Microsoft character encoding for simplified Chinese
Findings Reported
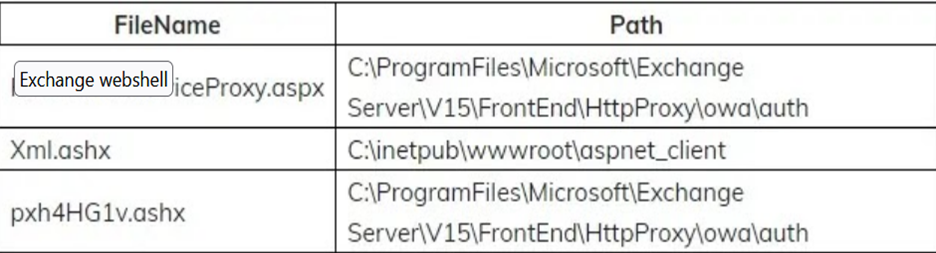
In one of the attacks, it is reported that the hacker / malicious actor also changed the content of the file RedirSuiteServiceProxy.aspx to web shell content. RedirSuiteServiceProxy.aspx is a legitimate file name available in the Exchange server.
See published table below for reference
Mitigation – Workarounds
Microsoft Security Response Center:
Microsoft published mitigation/workaround in the following article
Microsoft Exchange Online Customers do not need to take any action (Microsoft Exchange Online has detections and mitigation in place to protect customers).
On premises Microsoft Exchange customers should follow the instructions of the above post on the Microsoft Security Response Center’s official blog (follow the same URL listed above).
Recommendations – Suggested Actions
Microsoft Security Response Center
Please follow all the official directions/instructions given by the Microsoft Security Response Center in the following article. Stay updated by referring to the following article of the Microsoft’s blog.
Till any official hotfix/Patch is released be extra vigilant regarding any suspicious activity related to your affected assets.
References:
- https://www.zerodayinitiative.com/advisories/
- https://www.cyberkendra.com/2022/09/new-zero-day-on-microsoft-exchange.html
- https://borncity.com/win/2022/09/30/exchange-server-werden-ber-0-day-exploit-angegriffen-29-sept-2022/
- https://gteltsc.vn/blog/warning-new-attack-campaign-utilized-a-new-0day-rce-vulnerability-on-microsoft-exchange-server-12715.html
- https://thehackernews.com/2022/09/warning-new-unpatched-microsoft.html
- https://success.trendmicro.com/dcx/s/solution/000291651?language=en_US
- https://www.protocol.com/bulletins/microsoft-exchange-zero-day-vulnerability
- Customer Guidance for Reported Zero-day Vulnerabilities in Microsoft Exchange Server



