ACCESS THE GARTNER MDR GUIDE
Obrela has been included in Gartner's MDR Market Guide. Download to learn more about the latest MDR Service providers

OVERVIEW
Our MDR (Managed Detection and Response) is a mission-critical service that combines artificial and human intelligence to dynamically protect your digital universe and digital assets by identifying, predicting, and preventing cyber threats in real-time.
Utilizing a cloud-native PAAS technology stack, our purpose-built Global and Regional Cyber Resilience Operation Centers (ROCs) provide continuous visibility and situational awareness to ensure the security and availability of your business operations. When cyber threats are detected, rapid response services ensure operational resilience is restored and maintained with minimal client impact.
MDR PRODUCTS
MDR Core
A solid foundation for threat detection and response, centered around Microsoft Defender XDR. Ideal for establishing baseline protection across cloud and on-premises environments, enhanced with OBRELA’s advanced analytics and automation.
MDR CoreX
The most advanced, all-in-one, extended (X) MDR solution. Combines full Microsoft XDR and Sentinel capabilities with OBRELA’s proprietary threat content for unmatched visibility, speed, and accuracy—ensuring no blind spots across your digital estate.

MDR INFRA is a service designed to provide comprehensive protection against advanced cyber threats and attacks that target critical infrastructure components.
- 24×7 Managed Detection & Response
- Comprehensive visibility and readiness
- Scalable threat detection technology stack
- Built-in Automation and Orchestration
- MITRE ATT&CK framework
- 3D Visibility
- Unlimited Breadth and Depth
- Interoperability Guarantee.

MDR Cloud allows protection for 24/7 Managed Detection and Response for your Microsoft Cloud Ecosystem. With machine learning, at its core MDR Cloud ensures that data are parsed and monitored on a real time basis.
- Advanced Threat Detection
- 24×7 Managed Detection & Response
- Comprehensive Visibility
- Scale on Demand
- Custom Client content development
- Data Residency
- Rapid Customer onboarding
- Intelligence Driven MDR.

MDR for Vessels is purpose-built to address maritime cybersecurity challenges by providing a comprehensive cybersecurity solution that covers both Vessel IT and OT systems. MDR for vessels provides the highest level of protection against cyber threats and helps to minimize the risk of cyber incidents that could disrupt vessel operations or compromise sensitive data.
- Real-time Signature and Anomaly Based Threat Detection
- Alerts Criticality Prioritization
- OT Security Monitoring Integration
- Honeypot
- Bandwidth Management
- Solution Remote Access
- Vessel Logs Routing
- Web UI.

MDR for OT offers extended detection and response (XDR) that is rapidly deployed and works with diverse endpoints, IoT, OT, and industrial control system (ICS) devices. MDR OT takes security to the next level by looking at the devices on the network; where most attacks target. Active Threat Detection discovers devices, then using native language queries classifies all OT assets even when they aren’t communicating in the network.
- Advanced Threat Detection
- Deep Situational Awareness
- 24×7 Managed Detection & Response
- Compliance with industry regulations
- Cost-effective solution
- Comprehensive Tracking
- Interoperability
- Asset Management.

MDR for BRAND is an integral service to Obrela MDR products providing protection for all client external digital risks. It is supported by a 24×7, full-spectrum external threat intelligence, protection and response solution that provides comprehensive visibility and protection across the surface, deep and dark web.
Our MDR Brand service covers:
- Threat Intelligence
- Credential Exposure
- Impersonating Domains
- Certificate Issues
plus any of the following add-on modules:
- Data Loss Detection (DLD)
- Online Brand Security (OBS)
- Attack Surface Reduction (ASR)
The customer may select any combination of the above add-on modules on top of the core components.



MDR BROCHURE
Access the brochure and learn more
SERVICE CAPABILITIES
MDR (Managed Detection and Response) services combine technology, expertise, and proactive monitoring to provide organizations with a comprehensive suite of capabilities to detect, respond to, and mitigate cyber threats. By leveraging these services, organizations can bolster their cybersecurity defenses and effectively combat sophisticated and evolving threats
SOCaaS
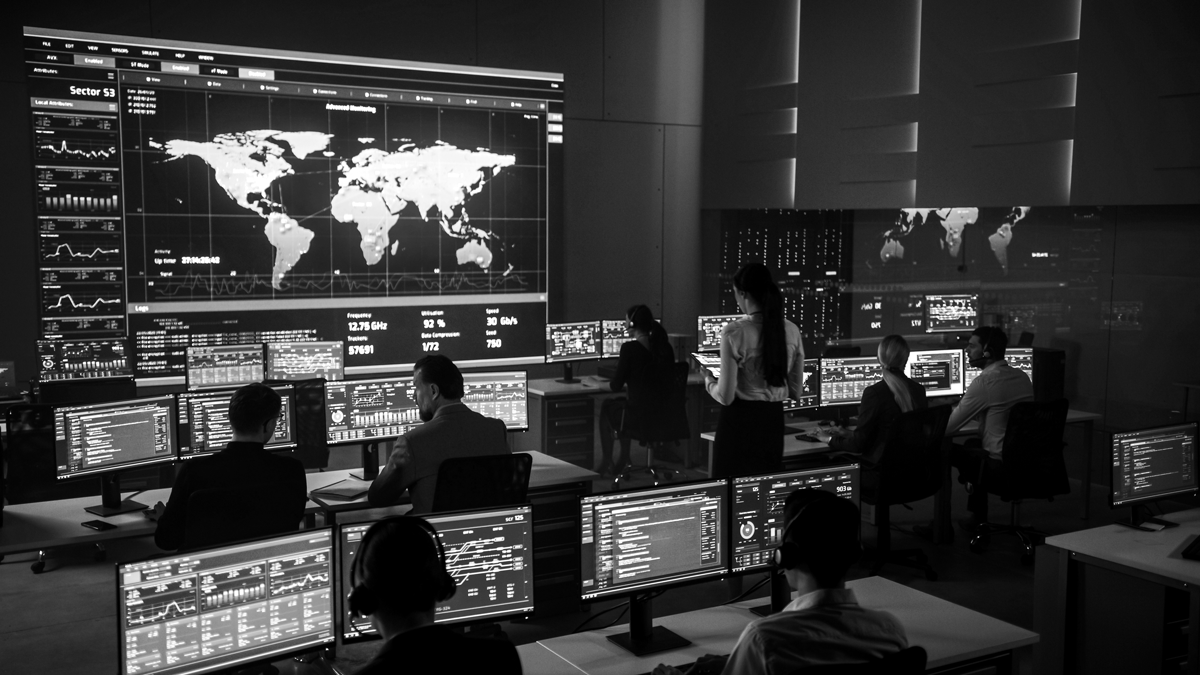
OBRELA’s Monitoring and Detection capability is the heartbeat of our MDR service. Operating 24/7/365 from our global and regional Cyber Resilience Operation Centers (ROCs), we deliver real-time situational awareness, powered by AI-enhanced analytics and expert threat analysts.
Learn More
Blue Team Support
The objective of Blue Team Support is to support Global and Regional Resilience Operation Centers with the necessary assistance to ensure effective incident management, escalation, and mitigation. This approach allows SOC teams to focus on their primary mission of continuous threat monitoring and incident response improving operational efficiency and resource optimization. Blue Team Support is a specialized security operations function designed to bolster Obrela’s Resilience Operations Centers (ROCs) on a global scale.
Learn More
Threat Hunting
Threat hunting services combine knowledge, intuition and automation to proactively search for covert signs of an active or attempted compromise. Leveraging advanced analytics and threat intelligence to investigate and manage malicious activities for our clients Obrela’s Threat Hunting team actively performs advanced Threat Hunts to identify threat actors and gaps in the organization infrastructure and security areas of further fine tuning. By combining the power of MDR with proactive threat hunting, we deliver comprehensive security coverage, enhanced threat detection, and rapid incident response to ensure your organization is well-equipped to combat sophisticated cyber threats.
Learn More
Proactive Incident Response
Proactive Incident ensures fast response and mitigation to cyber threats and is provided as part of the MDR service. Proactive incident response ensures fast response and mitigation to cyberthreats. With a Mean Time of less than 15 minutes our SOC Analysts and global Threat Hunting teams rapidly respond to investigate, contain, and mitigate threats.
Obrela is approved under the recognized UK national body CREST Cyber Security Incident Response (CSIR) scheme.

Platform Engineering & Support
The Platform Engineering and Support team encompasses all preventive maintenance and operations-driven technical tasks related to the Swordfish SaaS platform and the customers’ CPE and integrations with their systems. The Customers reach the team via Swordfish SRM for technical requests.
Learn More
Advanced Computer Security Incident Response
The Advanced Computer Security Incident Response team (CSIRT) provides support and guidance for eradication and containment of security incidents. An incident response capability also helps with dealing properly with legal issues that may arise during incidents.
Learn More
TECHNOLOGY STACK
Designed to revolutionize threat detection, response, and remediation across a wide array of security tools and platforms, our cutting-edge OPEN XDR Technology Stack creates a seamlessly unified ecosystem proving unprecedented levels of visibility, detection prowess, and incident response efficiency.

OPEN XDR TECH STACK
Obrela’s Open XDR Threat Detection Stack is a comprehensive multi-tenant platform developed by MDR professionals. Our state-of-the-art Open XDR Platform operated 24x7x365 is pro-actively monitoring network systems and applications looking for suspicious activity and notifying when security events require additional analysis, investigation, or action. The advanced real-time correlation and behavioral analysis capabilities of our platform identifies the relevance of any given event by placing it within context of who, what, where, when and why that event occurred, in order to derive its impact on business risk terms.

REVOLUTIONIZING THREAT DETECTION
Open XDR Threat Detection Stack:
- Enables security data processing and precise reporting at scale.
- Unleash the full potential of your security infrastructure as our MDR Technology Stack
- Harmonizes diverse security technologies, enabling them to work in perfect synergy.
- Gain a holistic understanding of your security landscape,
- Uncovers hidden threats and respond swiftly to incidents with confidence.
- Is highly scalable and can be extended to cover your complete digital universe.

TECHSTACK CAPABILITIES
Our advanced security technology stack leverages real-time human-augmented machine learning and threat analytics to deliver early detection of cyber threats. Designed with a focus on understanding the “attack logic” and exploitation path of advanced and determined adversaries, our solution harnesses powerful machine-learning techniques and encapsulated offensive and defensive expertise to continuously analyze and model relevant activity.
The technology uses modern techniques such as telemetry and APIs to exchange data and instructions over the digital universe, independently of the underlying technology stack and logical layers such as cloud, data centers, and digital assets. With over 1,000 collection methods available, the SWORDFISH DATA BUS enables comprehensive visibility across the entire customer attack surface, providing valuable insights.
Our exposure management service enhances detection capabilities by combining the latest threat intelligence with a deep understanding of the digital surface. This allows us to develop an accurate, prioritized list of current vulnerabilities, limiting exposure to both known and unknown threats.
Our technology stack is cloud-native and designed with a security-optimized data architecture that unifies the ingestion, parsing, and analysis of security data. This allows our platform-as-a-service (PAAS) architecture to dynamically scale, compute, and reserve resources as needed, ensuring maximum efficiency and security.
The technology stack provides Real-Time Threat Intelligence by parsing and fusing structured and unstructured security data from clients with global threat intelligence. This generates actionable intelligence for new, emerging, and advanced security threats, giving clients a unique advantage in predictability, preparation, and response.
SWORDFISH® Platform allows to orchestrate threat detection and response process, integrating existing service and ticket management systems that help clients implement and turn-up services to support the activities performed and the outcomes being delivered.
As a multitenant by-design Obrela allows for full multitenant views and dashboards, along with role-based access control and efficient user provisioning and management for the simultaneous support of multiple monitored environments. Efficient and seamless two-way integration with existing client security SOAR, workflow and ticketing systems.
Efficient and seamless two-way integration with existing client security SOAR, workflow and ticketing systems.
Our platform has the ability to perform “forensics on the fly”, run ultra-fast searches of raw and structured log data with speeds to Million Events per Second, without any concerns regarding technology risks, deployment, storage size monitoring, scalability, security, and performance, reducing hours of manual effort.

FAQS for MDR
MDR (Managed Detection and Response) is a cybersecurity service that provides organizations with 24/7 threat monitoring, detection, and incident response capabilities.
Unlike traditional security solutions that often rely on automated alerts, MDR combines advanced technology with human expertise to actively hunt for threats, investigate suspicious activities, and contain incidents before they can cause significant damage. Obrela’s MDR service leverages our proprietary technology and a team of experienced security analysts to provide proactive threat intelligence and rapid response.
MDR is suitable for organizations of all sizes that are concerned about the growing sophistication of cyber threats and lack the internal resources to effectively manage their security posture. It is particularly beneficial for organizations with sensitive data, regulatory compliance requirements, or those that are high-value targets for cybercriminals. Obrela’s MDR service is tailored to meet the specific needs of each client, regardless of their size or industry.
Obrela’s MDR service integrates seamlessly with your existing security infrastructure. We deploy advanced monitoring technology integrated with the Obrela Swordfish platform to collect and analyze security data from your network, endpoints, and cloud environments. Our 24/7 Security Operations Center (SOC) analysts then use this data to identify and investigate potential threats. When a threat is confirmed, our incident response team takes immediate action to contain the threat and minimize its impact.
Obrela’s MDR service is designed to detect a wide range of cyber threats, including advanced persistent threats (APTs), ransomware, malware, phishing attacks, insider threats, and zero-day exploits. We continuously update our threat intelligence database and employ advanced analytics to stay ahead of the latest threats.
Our incident response team is available 24/7 and is trained to respond to security incidents within minutes. We have established Service Level Agreements (SLAs) that guarantee a rapid response time to minimize the impact of any potential breach.
Yes, Obrela’s MDR service is designed to help organizations meet their compliance obligations. We understand the importance of data privacy and security, and our service adheres to industry best practices and relevant regulations, including GDPR, and others, depending on your specific requirements. Our team can assist you in implementing the necessary security controls to meet your compliance goals.
GDPR ComplianceObrela Swordfish is Obrela’s proprietary provisioning, orchestration and automation platform. It forms the core of our MDR service, providing real-time visibility into your security posture. Obrela Swordfish ingests and correlates data from various security sources, leveraging machine learning and AI to identify anomalies and patterns indicative of malicious activity.
Obrela’s MDR service is designed to integrate seamlessly with your existing security infrastructure, including firewalls, intrusion detection systems, and endpoint protection platforms. We offer flexible integration options to ensure compatibility with your environment.
Endpoint protectionObrela provides comprehensive reporting and real-time visibility into your security posture through the Obrela Swordfish platform. You will receive regular reports on detected threats, incidents, vulnerabilities, and overall security performance. Our dashboards provide a clear and concise overview of your security landscape.
You can request a personalized quote by clicking on the “Contact Us” button on our MDR page or by contacting our sales team directly through the “Contact Us” page. We will be happy to discuss your specific needs and provide you with a tailored solution.
Contact Us