Overview
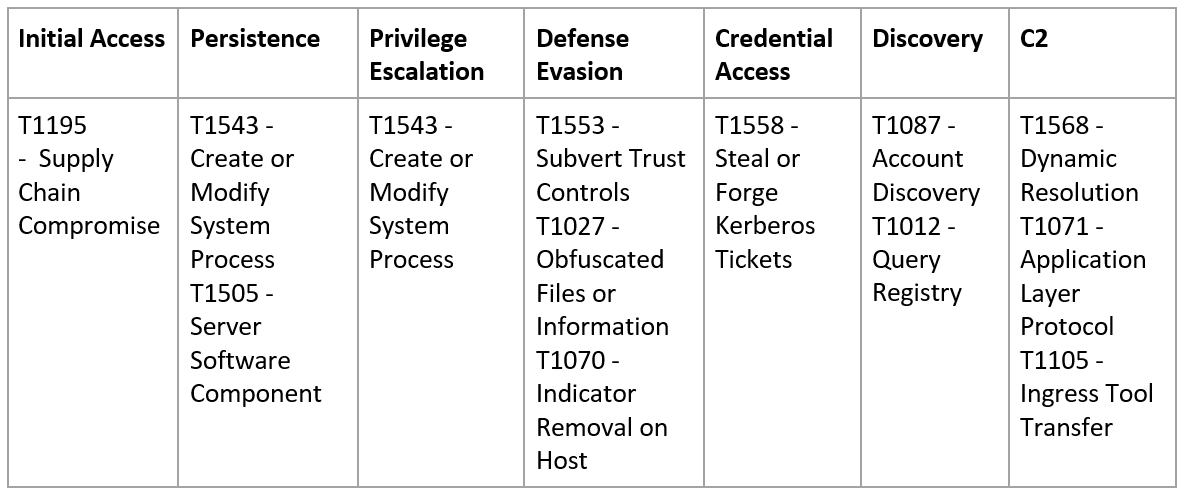
A sophisticated supply chain attack via trojanized update of SolarWinds products has been reported, affecting Orion Platform software builds 2019.4 HF 5, 2020.2 (with no hotfix installed), and 2020.2 HF 1. The campaign dubbed as “Sunburst” or “Solorigate”, attributed to UNC2452 has begun at least since Spring 2020 compromising organizations all around the globe. The MITRE ATT&CK techniques observed in the campaign can be summarized in the following table:
Anatomy of the attack
The compromised component of the SolarWinds Orion Platform is a digitally signed DLL suggesting that the addition of the benign code happened in the earlier stages of code development. The “SolarWinds.Orion.Core.BusinessLayer.dll” contained several mechanisms to ensure compromisation did not happen in a test or sandboxed environment but a real one. This initial reconnaissance contained (among other) techniques:
- Checks that no running processes or drivers related to security-related software were present
- Delay of execution by a random amount of time
- Affected domain verifications
- Checks that the host “api.solarwinds.com” resolves to an expected IP address
The backdoor code communicated via HTTP to receive instructions from a command and control (C2) server via a unique subdomain per victim, generated partly from information gathered from the affected domain. A pseudo random URI was also generated to resemble to junk traffic and evade detection. The communication with the C2 server contained functionalities ranging from manipulation of files and registry keys, to advanced persistence and full access to the compromised machines.
The attackers leveraged this sophisticated backdoor to move laterally to the compromised organization and follow standard privilege escalation and credential harvesting techniques by using built-in administrative tools or highly efficient third party hacking tools.
Indicators of compromise
Compromised installer
| Filename | SolarWinds-Core-v2019.4.5220-Hotfix5.msp |
| SHA256 | d0d626deb3f9484e649294a8dfa814c5568f846d5aa02d4cdad5d041a29d5600 |
Digitally signed DLL backdoor instances
| Filename | SolarWinds.Orion.Core.BusinessLayer.dll |
| SHA256 | e0b9eda35f01c1540134aba9195e7e6393286dde3e001fce36fb661cc346b91da58d02465e26bdd3a839fd90e4b317eece431d28cab203bbdde569e11247d9e232519b85c0b422e4656de6e6c41878e95fd95026267daab4215ee59c107d6c77dab758bf98d9b36fa057a66cd0284737abf89857b73ca89280267ee7caf62f3beb6fab5a2964c5817fb239a7a5079cabca0a00464fb3e07155f28b0a57a2c0edc09040d35630d75dfef0f804f320f8b3d16a481071076918e9b236a321c1ea77ffdbdd460420972fd2926a7f460c198523480bc6279dd6cca177230db18748e8b8a05cc492f70ffa4adcd446b693d5aa2b71dc4fa2bf5022bf60d7b13884f66620e35055113dac104d2bb02d4e7e33413fae0e5a426e0eea0dfd2c1dce692fd90f5d7e6dfdd62c83eb096ba193b5ae394001bac036745495674156ead6557589 |
DGA-generated C2s as subdomains of:
*.avsvmcloud[.]com
C2 domains found
- databasegalore[.]com
- deftsecurity[.]com
- digitalcollege[.]org
- freescanonline[.]com
- highdatabase[.]com
- incomeupdate[.]com
- panhardware[.]com
- thedoccloud[.]com
- virtualdataserver[.]com
- websitetheme[.]com
- zupertech[.]com
Mitigation actions
- Visit the SolarWinds customer portal to check which of your product installations are compromised and upgrade the following as soon as possible:
- Orion Platform v2020.2 with no hotfix or 2020.2 HF 1 to Orion Platform version 2020.2.1 HF 2
- Orion Platform v2019.4 HF 5 to update to Orion Platform 2019.4 HF 6
- Reimage operating systems hosting all instances of SolarWinds Orion versions 2019.4 through 2020.2.1 HF1
- Isolate SolarWinds Orion products, versions 2019.4 through 2020.2.1 HF1, from your network.
- Identify accounts that have been used on the affected device and consider them compromised
- Identify the existence of “SolarWinds.Orion.Core.BusinessLayer.dll” and “C:\WINDOWS\SysWOW64\netsetupsvc.dll”.
- Block all traffic to and from hosts where any version of SolarWinds Orion software has been installed
- Make sure you have updated your security controls to the latest versions
Final notes
In a collaborative effort to prevent the malware from continuing to operate, security community have proceed to take over the avsvmcloud[.]com domain, thus preventing compromised networks from communicating with the attackers. However, this killswitch will not remove the actor from victim networks where they have established persistence; it will make it more difficult for the actor to leverage the previously distributed versions. During the investigation of the “Sunburst” campaign, a second malware dubbed “Supernova” from a different hacking group is suspected to be present in Orion software. As the investigation is currently on-going, our teams remain alerted and follow the latest threat intelligence feeds to fins new indicators of compromise.
Access to services hosted in cloud infrastructure was also obtained by the attackers, hence organizations should take actions to improve their security posture by enabling security features and capabilities. Obrela Security Industries have recently discussed the topic of cyber-attacks in cloud infrastructure and development pipelines in ItDevPro Connections 2020 conference, by presenting key considerations on monitoring of cloud services to identify and better respond to incidents. The link of the presentation can be found here.
Disclaimer
In order to assure our clients that Obrela Security industries has not been impacted by this supply chain attack, we would like to inform you that no SolarWinds software is being used in any parts of our network infrastructure.



