The Hunt for Blue October (Part 1)
Anatomy of the attack
Since mid-October many Greek organizations have been targets of the latest Emotet campaign. OBRELA-CSIRT has been relentlessly analyzing malware samples and monitoring network traffic since the beginning of the campaign. We have observed a shift from its original keylogging, proxy sniffing techniques into more stealthy and intrusive ones like code packing, persistence mechanisms and cryptographic key creation that is indicative of ransomware attack staging. Emotet is a Trojan commonly functioning as a downloader or dropper of other malware. This increase has rendered Emotet one of the most prevalent ongoing threats.
The campaign structure as of this moment can be summarized in the following picture
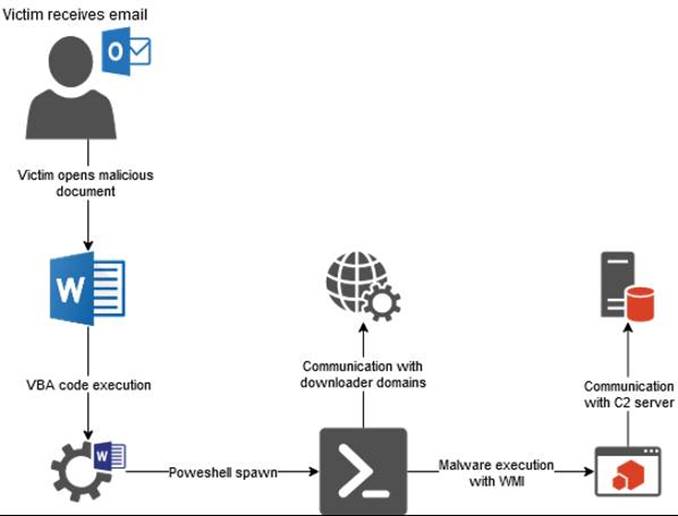
Breakdown of the campaign
TTPs (Tactics, Techniques, Procedures) observed
MITRE ATT&CK related techniques currently utilized in the campaign
Emotet Indicators of Compromise
Current Emotet campaign is tricking the victims by impersonating known entities of their environment (partner organizations, etc..) into clicking a link to download a malicious document or opening a malicious Word document contained as attachment in the email.
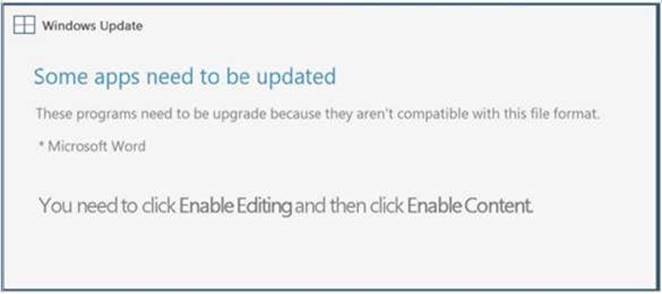
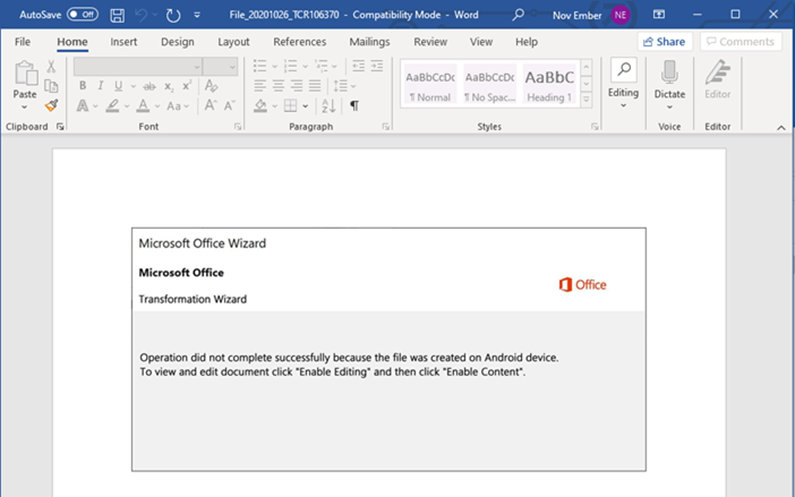
A typical malicious document is asking for updates like the following:
Payload Domains
After the document has been opened by the victim, out-bound connections with the following domains is established through PowerShell, to download the payload: the Emotet malware
- hxxp://hashilife.com/sitepage/GY/
- hxxp://anjia-ceramics.com/aliner-camper/K/
- hxxps://monicasharma.info/reviewl/i/
- hxxp://adidasyeezy.store/welph/m/@
- hxxp://econews.treegle.org/how-to/2V/
- hxxp://quicktowtowing.com/wp-content/mu-plugins/uMM/
- hxxps://timsonntag.com/cgi-bin/g/
- hxxp://yourprivatelife.com/wp-admin/sq/
- hxxps://www.firsattrade.com/wp-content/pI/
- hxxps://ashiq.xyz/wp-content/qX/
- hxxps://aryabhattahighschool.com/wp-includes/C1x/@
- hxxps://angelsandfriends.com/wp-includes/d31/
- hxxps://dmccainlaw.com/wp-content/3/
- hxxps://tvcableinternetdeal.com/wp-content/cu/
- hxxp://innhanmacquanaogiare.com/wp-includes/Jh1/
- hxxp://www.edgeclothingmcr.com/indexing/c9/
- hxxps://thepremiumplace.com/wp-content/5/
- hxxps://florinconsultancy.com/wp-content/1/
- hxxps://udaysolopiano.com/wp-content/J/
- hxxps://sanayate.com/wp-includes/hd/
- hxxps://www.jorgecoronel.com/webmaster/kYH/
- hxxp://michaelandrewsbakery.com/wp-admin/M/
- hxxp://forsalebyowner247.com/wp-includes/8m/
- hxxp://webgisjambi.com/wp-content/uploads/V5a/
- hxxps://tigerstormtraffic.com/wp-includes/h23/
- hxxp://twogirlscleaning.com/openbayl/KaI/
- hxxp://online2u.biz/ogretmenevi/4Yj/
- hxxps://caglayann.com/wp-admin/Xt1/
- hxxps://crechereviver.org/siteunavailable/3/
- hxxps://logistician.org/wp-admin/aGQ/
- hxxps://passionpastry.com/wp-admin/n/
- hxxps://ivytheme.com/wp-admin/LyR/
- hxxps://secuado.com/wp-content/plugins/apikey/6/
- hxxps://m-tash.com/wp-includes/9/
- hxxp://plakatjogja.com/wp-content/X/
- hxxp://vnadevelopers.com/wp-admin/BF/
- hxxp://nursesweekparty.com/wp-includes/bQR
- hxxps://www.hodmunha.info/wp-includes/Ce/
- hxxps://novaworldsmuine.com/khudothiaquacity.com/a
C2 Servers
After the malware samples are downloaded, they are executed through WMI process to establish communication with the following C2 servers, performing keylogging and proxy inspection activities.
| 81.214.253.80 94.23.62.116 45.16.226.117 190.92.122.226 70.39.251.94 120.72.18.91 192.175.111.212 193.251.77.110 81.214.253.80 187.162.248.237 70.32.84.74 173.68.199.157 172.86.186.21 181.123.6.86 46.101.58.37 46.105.114.137 174.118.202.24 37.187.161.206 | 212.71.237.140 172.104.169.32 193.251.77.110 103.13.224.53 77.78.196.173 82.76.111.249 181.61.182.143 177.107.79.214 190.188.245.242 74.135.120.91 68.183.190.199 177.23.7.151 98.103.204.12 85.214.26.7 120.72.18.91 197.232.36.108 50.28.51.143 83.169.21.32 |
In all the analyzed samples, the communication between the C2 servers and the infected machines is done with the same User-Agent thus linking the incidents of various organizations, into the same Emotet campaign.
| User Agent | Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E) |
OBRELA-CSIRT is noticing an alarming twist in recently analyzed samples. The Emotet payloads since Monday 26/10, employ persistence mechanisms in registry and services to survive reboot on Windows systems and utilized internal Windows APIs to create cryptographic keys. The latter is extremely disturbing, given that this activity is relevant to ransomware staging as these keys will be used to lock files within infected systems with unique and asymmetric encryption, unless ransom is paid.
Recommendations
- Exercise extreme caution with attachments and links in emails.
- Ensure anti-virus software and associated detection databased are up to date.
- Keep applications and operating systems running at the current released patch level.
- Restrict PowerShell and WMI usage to users endpoints to the absolute need for administrative purposes.
- Consider blocking and or setting up detection for all URL and IP based IoCs on your security controls.
Our team will conclude The Hunt for Blue October saga in Part 2, where technical details and attack insights will be presented.



