">
">SWORDFISH
YOUR 'ERP' FOR CYBER
Just like the ERP systems evolved delivering a centralized and consolidated approach to information, allowing decision-makers to view key performance indicators and make insightful decisions, we at Obrela envisioned, designed, and engineered an ERP for Cyber Risk and Operations Management.
OUR TECHNOLOGY
SWORDFISH® can help organizations to manage and orchestrate the diverse facets of cybersecurity (preventive, reactive) under a new comprehensive approach. SWORDFISH® brings predictability to the seemingly uncertain, allowing organizations to orchestrate and control every element of their cyber defense through a single platform.
Using embedded content and a wide variety of applications for governance, risk and compliance SWORDFISH® consolidates all functions and security related data under a single pane of glass helping organizations get instant visibility and situational awareness focusing on operational risks and outcomes that impact their business objectives.
SWORDFISH® currently serves as our prime Security-as-a-Service (SecaaS) Provisioning Platform and is closely integrated with all our service offerings today acting as a unified Operations and Service Provisioning Fabric, simplifying service consumption, performance evaluation, and the participation in critical mission activities for clients and stakeholders.
Orchestrate your cyber controls under a single data lake with real time analytics that support informed decisions based on real time risk management.
THE COMPONENTS | PREDICTABILITY OVER UNCERTAINTY
SWORDFISH® Platform (PAAS) serves as the provisioning and delivery layer of our services. Obrela uses SWORDFISH® for MDR to deliver comprehensive MDR services to its clients. This powerful solution acts as a central layer that enables the efficient coordination of security operations to address risk management, supply chain security, and access management.
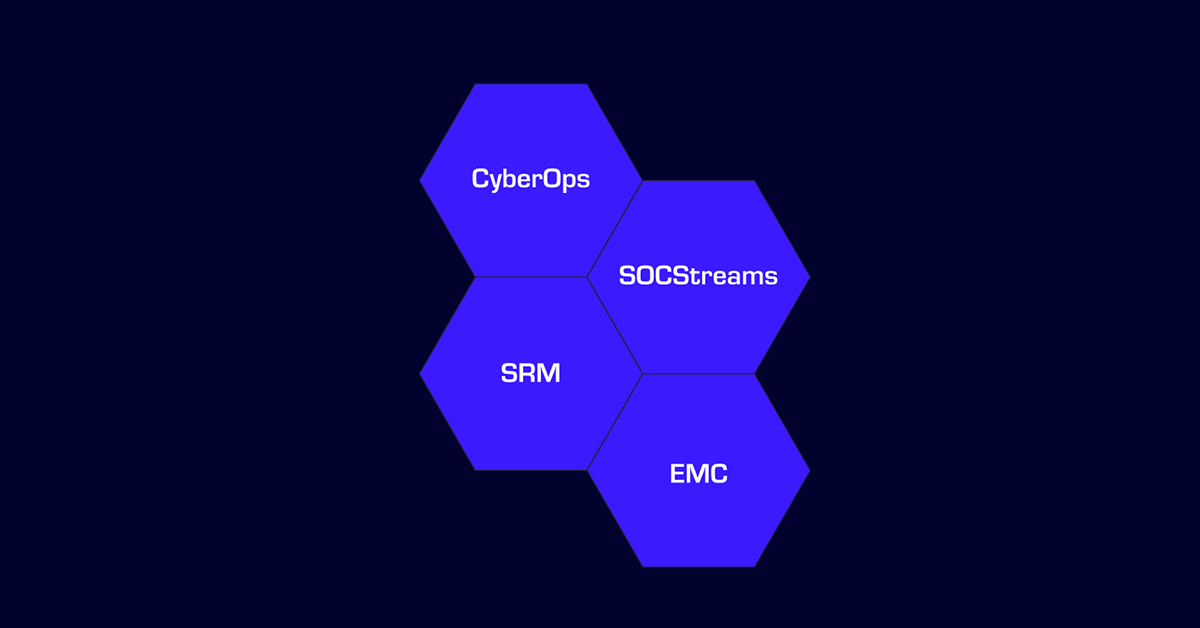
SWORDFISH® MDR Modules

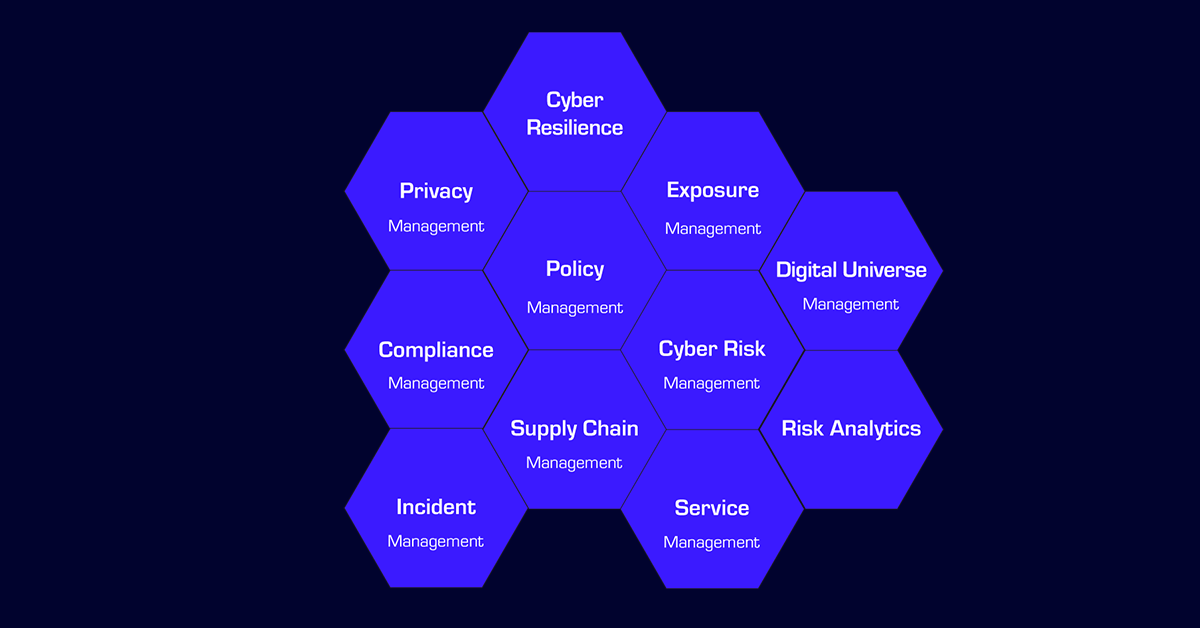
OBRELA’s SWORDFISH® cloud-native platform provides organizations with a centralized and real-time view of their security, compliance, privacy, and business risks. The platform can cover different aspects of security, privacy, and risk, and enable data and workflow fusion for a comprehensive risk management approach. It can be attuned to the versatile and dynamically changing needs of enterprises as a integrated cyber risk management platform that orchestrates controls in the diverse facets of cybersecurity operations.
Swordfish MRC Modules:

SWORDFISH® IN ACTION
An overview of the platform capabilities to help you consolidate operations achieving security over everything
Contact Us


BOOK A DEMO

DIGITAL UNIVERSE REPORT
Obrela’s data correlation capabilities combined with our deeply sophisticated analysis result in a unique insight upon the threat landscape (Highlight stats for 2024)
31%
Malware attacks
18%
Increase of suspicious internal activity
33%
Insider attacks in Europe
31%
Targeted attacks in MENA
25%
BruteForce attacks in lottery services