Anastasios Stasinopoulos from OBRELA LABS Team discovered a security flaw that affects Apache Superset (before 3.0.4, from 3.1.0 before 3.1.1), an open-source modern data exploration and visualization platform.
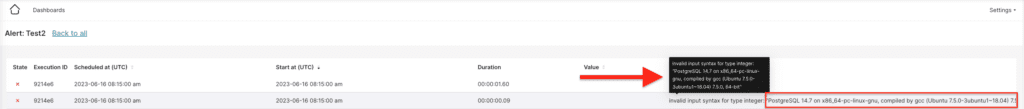
Apache Superset error handling can be manipulated in order to allow data retrieval from the backend database. More specifically, it was identified that if an arbitrary VARCHAR value is casted to an INT or DECIMAL on “add alert” functionality, the produced error discloses the actual result of the SQL query.
Successful exploitation of this vulnerability, allows an authenticated user with privileges to create Alerts on Alerts & Reports functionality, to gain unauthorized access to the stored data in the backend database.
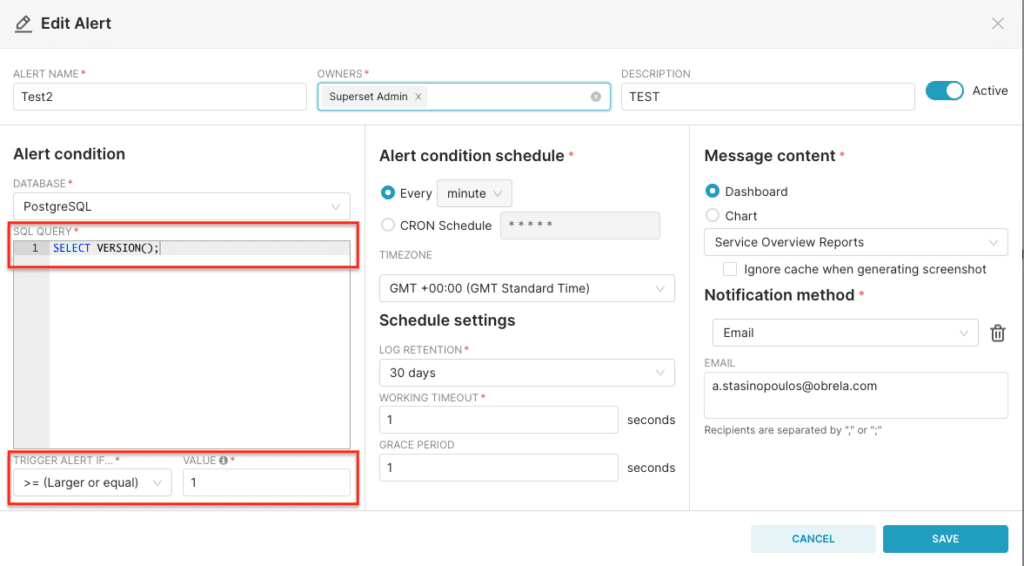
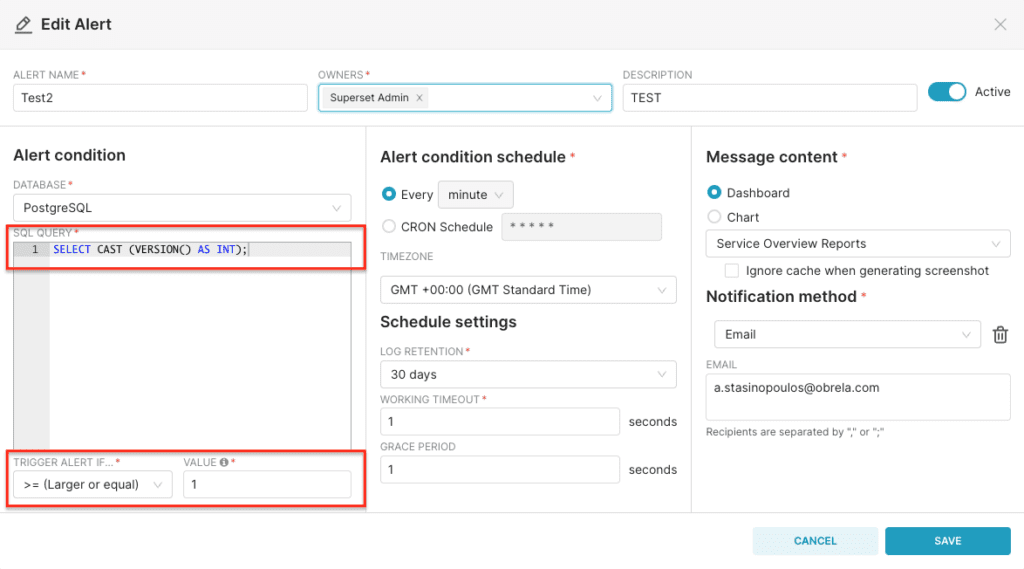
Proof of Concept: The query “SELECT VERSION();” does not print any results on the dashboard (intended behavior). The query “SELECT CAST (VERSION() AS INT);” though, prints the results of VERSION() in the respective error message that is triggered due to casting.
VARCHAR query input:
Alert’s Execution Logs:
Casting to INT input:
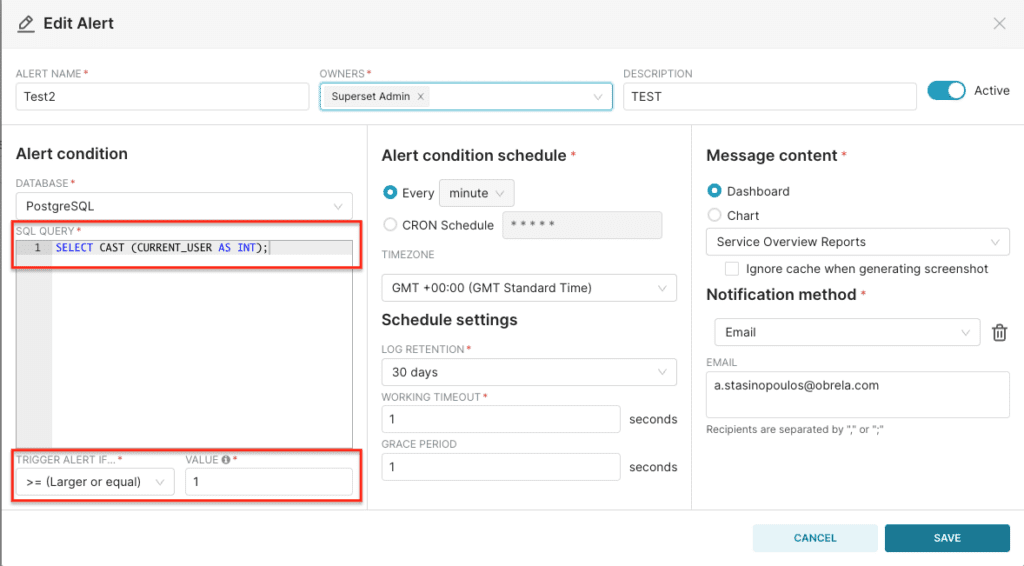
This behavior can be exploited in order to retrieve the results of arbitrary SQL queries.
Casting to INT input:
Alert’s Execution Logs:
The software vendor was informed prior to public disclosure of the vulnerability, which was registered afterwards with a CVE record: CVE-2024-27315.
Discovery and public disclosure timeline:
- 2023-06-16 – Discovery
- 2023-06-19 – Vendor Contact
- 2024-02-05 – Vendor Triaged Vulnerability
- 2024-02-28 – Apache Software Foundation Assigned CVE